HTTPS is becoming increasingly important for every website out there on the internet and even on intranet sites. As HTTPS prevents eavesdropping and MiTM attacks. All major browsers discourage visiting HTTP-only websites and there are multiple initiatives to issue TLS/SSL certificates needed for HTTPS to as many websites as possible… except to websites based in US-sanctioned countries.
The prime example of excluded from the secure internet due to US sanctions is the DPRK. While the China-based DPRK website Uriminzokkiri has a valid TLS/SSL certificate, all DPRK-based websites such as Naenara, KCNA, Voice of Korea and Rodong Sinmun do not have access to any kind of TLS/SSL certificate.
What do we do? Try to take action via our US-based comrades? Try to start our own CA?
Starting your own CA would be pointless for those outside of the DPRK. It would get labeled as being used by “authoritarian regimes”, the technical people for Chrome, Firefox, Edge would ask why they should add it and act like it’s going to be used for nefarious ends and probably refuse to add it to their certificate stores.
Without that and without a state-distributed operating system or state-browser bundle you can distribute to people with it pre-installed everyone would have to install the CA root, trust it in their browser, etc. And most people aren’t going to do that they’re just going to see the scary untrusted cert warning and back away from the website. Them adding untrusted CA generated certificates would literally hurt their ability to get people to look at them.
Yes, starting a CA just for DPRK/Russian/other US-sanctioned sites wouldn’t work, but having a large enough CA would make it impossible for Google/Mozilla/Microsoft to say no to the inclusion.
As Let’s Encrypt (and the Internet Security Research Group) have been pushing HTTPS the most, I think we should apply pressure to them to relocate to a country that allows them to issue TLS certificates to websites based in US-sanctioned countries. As the ISRG is currently based in the US, I don’t think they can currently bypass those US sanctions despite them wanting to be as politically neutral as possible.
Knowing very little of the specifics, it would be trivial for the DPRK to set up their own CA. They probably do have a CA. The issue is that Western software distributors (operating systems, browsers, etc) probably wouldn’t want to include DPRK CAs in their CA stores. Likewise, organizations within the DPRK probably don’t trust CAs located in the West, even if they are operated by nominally allied organizations. This problem can be solved by including their domestic CAs in software distributions (they have their own Linux distro, after all) and distributing tools to easily install them on other operating systems.
Do you know if this applies just to outward-facing websites, or is this a problem across the board on their domestic networks?
There’s not much you can do except advocate for the use of DANE in browsers: this lets site operators pin their certificates in DNS. It is tricky because it is linked to the operation of DNSSEC at the moment. Have a read:
https://en.m.wikipedia.org/wiki/DNS-based_Authentication_of_Named_Entities
Websites in the DPRK’s intranet have access to SSL certificates. Their root CA for all websites within the DPRK is the Pyongyang University of Science and Technology if I’m not mistaken. They also issue certs for their own websites on the internet.
The next step, in this situation, is pushing for certificates from sanctioned countries to be included into free software web browsers. I’d even argue that forking Firefox just to do this is justified, though supporting an up-to-date fork is no easy task, even for small changes like changing the default cert store.
Voice of Korea does in fact have a TLS certificate. You may have to specify https:// manually though.
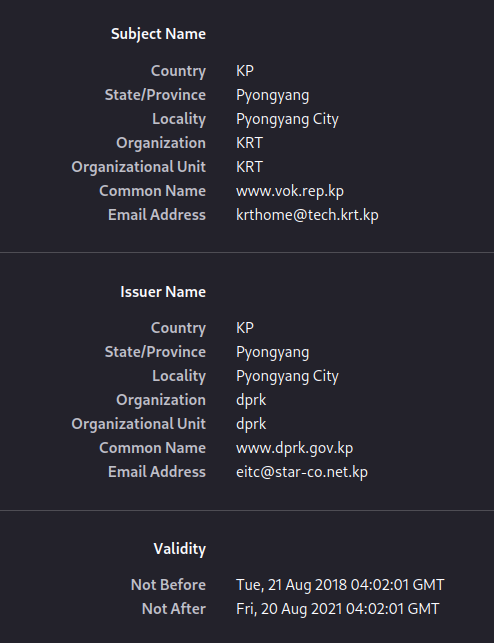
It’s still going to make western web browsers mad because It’s technically self-signed. Also it expired almost 2 years ago.
Funny that http sites are treated as safer than https with self-signed certificate.
Not really. Anyone can self-sign a certificate, even someone conducting a Man-in-the-Middle.
By allowing self-signed certs, the average user could be lulled into a false sense of security. These users could easily believe that they have connected directly, securely, and safely to a website, when they have actually connected to an impostor site or a MitM proxy.
Sure, but the communication is still encrypted. Apart from the sense of security, it is at least as safe as just http. So I find it funny that when you access http site you don’t get a warning about the site being unsafe, but with a self-signed certificate you do.
Sure, but the communication is still encrypted.
Good point, but what’s the point in encrypting data if it just goes straight onto the hands of an adversary?
Sure, other adversaries can’t also steal a copy of the same data, but I’m not sure if that’s really a concern if you’ve just handed your bank account login to gangsters. They can’t steal your savings if someone else already stole them first, if you catch my drift. And if it’s some other random login-password combos, you’ll just end up with your password in two darkweb dumps rather than one.
I’m not saying that you’re wrong, but it’s a relatively minor distinction. Both self-encrypted https and plain http deserve big warnings for end-users.
I suppose it’s all pointless anyway, now that I think about it. The NSA’s BULLRUN can purportedly break TLS-based encryption. I’d wager that they backdoored themselves at the cert-isssuers, Clipper-chip style.
So I find it funny that when you access http site you don’t get a warning about the site being unsafe…
What browser are you using? I use Firefox, Mullvad Browser, and occasionally Chromium (all on Linux), and they all complain about plain http sites (as far as I recall).
I use Firefox and if I visit http site I don’t get any warning, only the red symbol next to the address bar. If I visit https site with non-valid certificate, I get the site where I have to click I understand the risk or something like that to continue.
To be honest, I don’t really want it. I often connect to http sites when doing development, so this would be just a pain. But it was not on, and I didn’t change it, although I guess it is possible that that is the default NixOS setting.





