You’re forced to use Cloudflare. Don’t they track … everything?
Update: Apple’s role in adding extra location data to your request has been added to this post
Apple and a couple other providers have been experimenting with a multi-hop system of making your connections private.
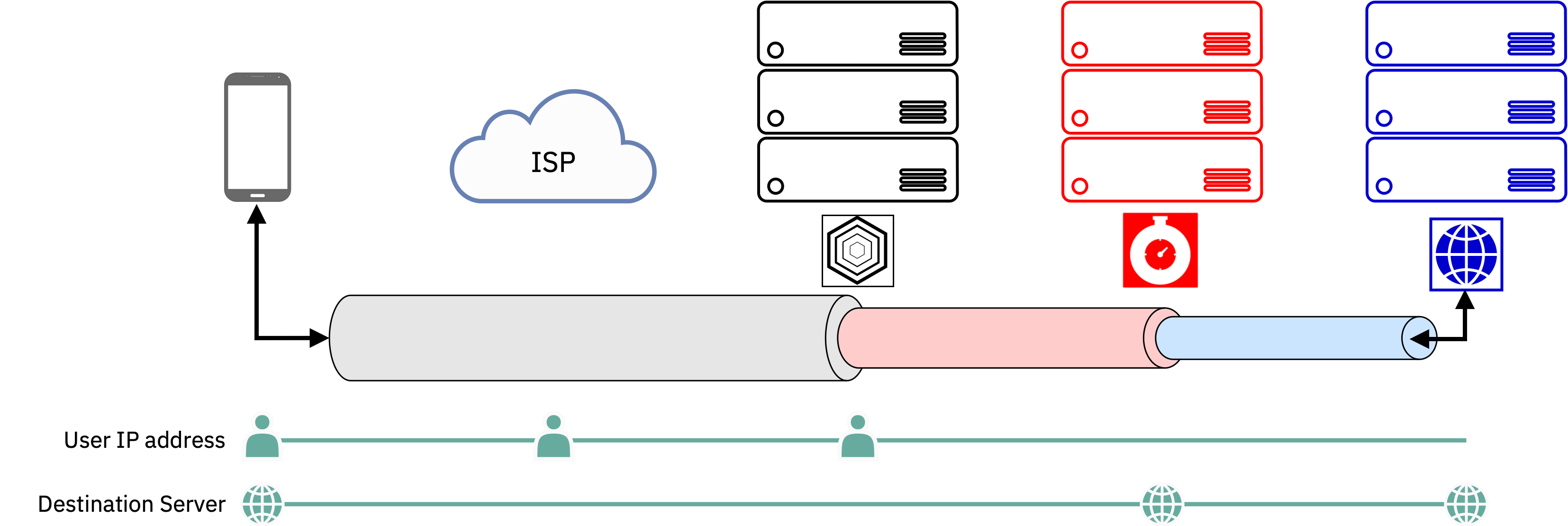
Here’s what a competitor, Invisiv, says.
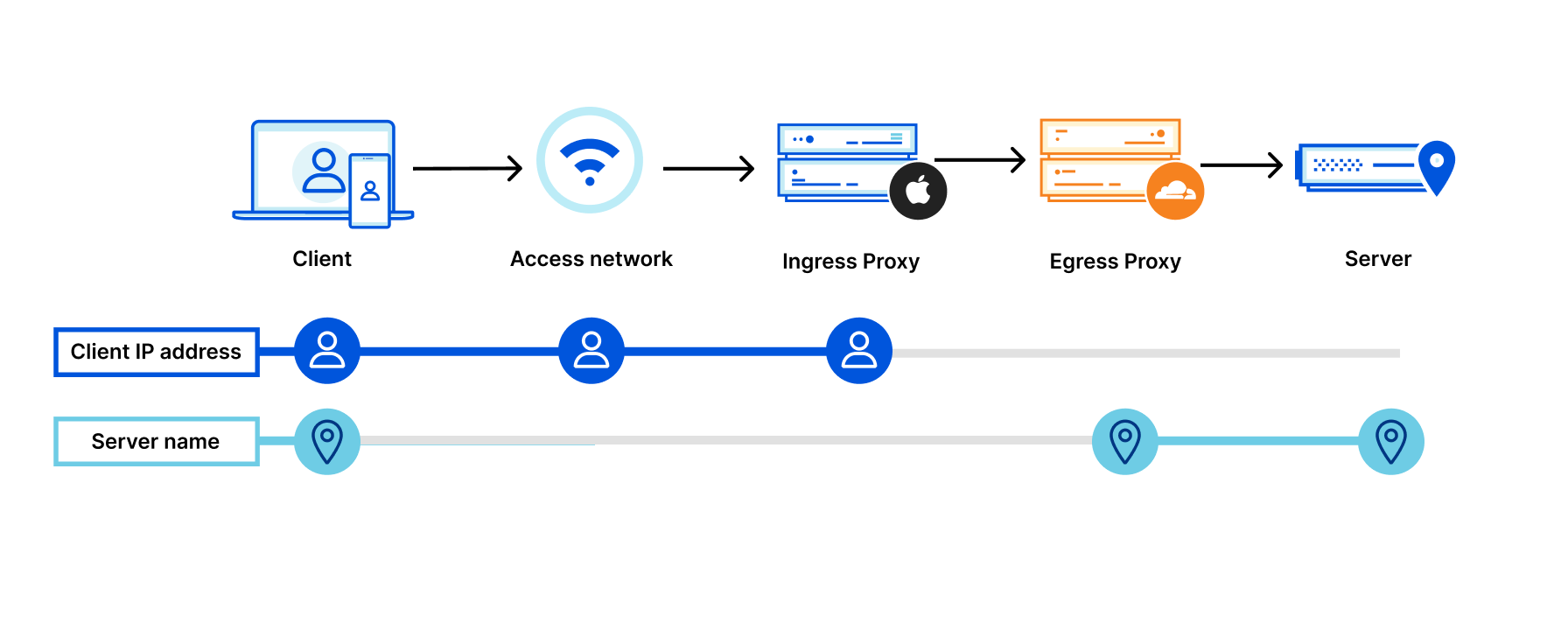
Both pages are pretty hard to parse (IMO Cloudflare uses more jargony language: “ingress”/“egress server” - really?) but they get to the same point.
Your data takes a path like this
- Your computer, your IP address, your message to a destination gets encrypted in a couple layers and passed on.
- Your ISP knows exactly who you are and that you’re reaching out to server 1. They can’t see your data but to them, you’re using a VPN probably.
- The first server also necessarily knows who you are, unpacks one layer of your request and sends it on to a second server (in Invisiv’s case, Fastly; in Apple’s, Cloudflare).
- The second server now knows that data was requested from the first server, and it can see the name of the domain you’re requesting (YouTube, for example) but because the request came from the first server, it theoretically won’t know it’s you making that request
- The data moves on from the second server to the destination, with the destination only knowing it’s receiving data from the second server, and not knowing about the first server.
The obvious issues here:
- Do you trust the people providing the multi-hop VPN-like service?
- Do you trust the two servers, which have necessarily entered into an agreement of some sort, to not collaborate regarding transmitting data?
- How easy is it to audit the code we can see?
- What else is going on with your data?
In the case of Apple/Cloudflare, reputation is rather poor. From PRISM to false advertising to notification telemetry, Apple hasn’t exactly delivered on their promise. In terms of Invisiv, the company has some big names on board but Fastly and Cloudflare both have a rather significant grip on the internet (with Cloudflare’s being bigger) but any CDN gets a good view into personal data most of the time.
Update: in the case of Cloudflare/Apple, Apple adds additional location data to your request, making its “private” relay leak approximate location data the same way your IP address could leak it. To wit:
Apple relays geolocate user IP addresses and translate them into a “geohash”. Geohashes are compact representations of latitude and longitude.
But on the bright side: a VPN has far more issues than either of these, as it’s basically #4 above except the same service also has your identity by necessity. An untrustworthy VPN is as harmful as an untrustworthy ISP, with very little separating them.
Just wanted to chip in and say, what a great comment! 👌
Ah, so it’s just corporate Tor. Mega gross.
A less private Tor or a hyper VPN.
A bit less private because things are going through one fewer hop, in addition to having to sign up. In my experience with Invisiv, it’s much faster and more reliable than Tor, but slower and much less stable than a traditional VPN.
It would be cool if more commercial VPN companies adopted this kind of tech.
iVPN has Multi-hop feature, which looks similar to what you described in the post. Speaking of it, thanks for the detailed explanation!
But in the case of iVPN, do they run both of the servers themselves? That’s always what I wondered about.
They rent their servers, so it depends on what you consider as running the server. They have virtual access to it, but they don’t own the hardware. At least, that’s the case for countries I checked, maybe they have their own servers somewhere too.
My main concern is that cloudflare knows what content it is serving and it is certainly fingerprinting your browser. So regardless of how you request the data, cloudflare knows.
yea but cloudflares probably gonna know anyway cause they serve a large portion of the Internet anyway
After reading their documentation a little closer, I discovered something else unsavory about Private Relay: it “relays” your approximate location, as it could usually be derived from your IP address.
Updated my comment.
Hate to break it to you but all the major CDN providers do the exact same things. My employer runs multiple websites mainly for US and European users. We use Akamai for both CDN and WAF services. For any CDN and/or WAF to operate properly it needs access to unencrypted content. Part of Akamais WAF tools includes what they call Bot Manager, which can identify traffic coming from over 1000 known bots and can also classify unknown ones. Part of how it works is by browser fingerprinting as well as TLS session fingerprinting and other proprietary fingerprinting.
So any time you visit a large website you’re likely being fingerprinted and otherwise analyzed by the CDN and security tools used by those sites.
deleted by creator
I see Apple in the name, so how private? Wide open.
Damn i should’ve read into this a bit more. Didn’t see they used cloudflare
I will say that Apple is 100 percent collecting your data. Health, financial, biometric, anything you put in an Apple Device is subject. Like most large companies, the are probably also purchasing profile data from Acxiom and Experian.
I don’t know if they are doing it with this service but Apple is definitely not respecting your privacy. If you are concerned about privacy, you’re better off trying to use more specialized tools for a job than any singular ecosystem. Apple wants everybody to be in their single ecosystem to better build profiles in their systems.
Request: Your IP > Apple (1st) relay node > 3rd party (2nd) relay node > Website
Response: Your IP < Apple (1st) relay node < 3rd party (2nd) relay node < Website
Whoever has access to both relay nodes, can easily track you end-to-end.
As for Apple, they claim the 1st relay node is owned by them, and 2nd relay node is owned by 3rd party. (Source: https://www.apple.com/icloud/docs/iCloud_Private_Relay_Overview_Dec2021.pdf)
In theory, it should not be a privacy concern because -
- Website will see the request coming from 2nd relay node’s IP.
- 2nd relay node will see the request is coming from Apple (1st) relay node’s IP.
- So, only Apple knows your IP.






